- 1. Background
- 1.1. How do you pronounce 'Valgrind'?
- 1.2. Where does the name 'Valgrind' come from?
- 2. Compiling, installing and configuring
- 2.1. When I trying building Valgrind, 'make' dies partway with an assertion failure, something like this:
- 2.2. When I try to build Valgrind, 'make' fails with/usr/bin/ld: cannot find -lccollect2: ld returned 1 exit status
Mission Statement. This project aims at making the Valgrind tool suite available on Microsoft Windows. The project founder believes that is it technically possible to run Valgrind natively on Windows, and that a coordinated, collaborative effort by open source developers will eventually deliver a stable and production-ready release. Valgrind Publisher: to record valgrind xml reports Those two things work independently from each other. So if your build system already calls valgrind (as part of your unit tests or whatever) just use the publisher to record and analyze the xml reports. Programs run OK on Valgrind, but at exit produce a bunch of errors involving libcfreeres and then die with a segmentation fault. When the program exits, Valgrind runs the procedure libcfreeres in glibc. This is a hook for memory debuggers, so they can ask glibc to free up any memory it has used. Nov 21, 2019 Valgrind is a debugging tool which is available on Linux, it's an opensource project and is free to use. Valgrind helps with memory leak detection, threading bugs and can help optimize code using its profiling support.
- 3. Valgrind aborts unexpectedly
- 3.1. Programs run OK on Valgrind, but at exit produce a bunch of errors involving __libc_freeres() and then die with a segmentation fault.
- 3.2. My (buggy) program dies like this:
- 3.3. My program dies, printing a message like this along the way:
- 3.4. I tried running a Java program (or another program that uses a just-in-time compiler) under Valgrind but something went wrong. Does Valgrind handle such programs?
- 4. Valgrind behaves unexpectedly
- 4.1. My program uses the C++ STL and string classes. Valgrind reports 'still reachable' memory leaks involving these classes at the exit of the program, but there should be none.
- 4.2. The stack traces given by Memcheck (or another tool) aren't helpful. How can I improve them?
- 4.3. The stack traces given by Memcheck (or another tool) seem to have the wrong function name in them. What's happening?
- 5. Memcheck doesn't find my bug
- 5.1. I try running 'valgrind --tool=memcheck my_program' and get Valgrind's startup message, but I don't get any errors and I know my program has errors.
- 5.2. Why doesn't Memcheck find the array overruns in this program?
- 6. Miscellaneous
- 6.1. I tried writing a suppression but it didn't work. Can you write my suppression for me?
- 6.2. With Memcheck's memory leak detector, what's the difference between 'definitely lost', 'possibly lost', 'still reachable', and 'suppressed'?
- 7. How To Get Further Assistance
1. Background | |
| 1.1. How do you pronounce 'Valgrind'? 1.2. Where does the name 'Valgrind' come from? | |
| 1.1. | How do you pronounce 'Valgrind'? |
The 'Val' as in the world 'value'. The 'grind' is pronounced with a short 'i' -- ie. 'grinned' (rhymes with 'tinned') rather than 'grined' (rhymes with 'find'). Don't feel bad: almost everyone gets it wrong at first. | |
| 1.2. | Where does the name 'Valgrind' come from? |
From Nordic mythology. Originally (before release) the project was named Heimdall, after the watchman of the Nordic gods. He could 'see a hundred miles by day or night, hear the grass growing, see the wool growing on a sheep's back' (etc). This would have been a great name, but it was already taken by a security package 'Heimdal'. Keeping with the Nordic theme, Valgrind was chosen. Valgrind is the name of the main entrance to Valhalla (the Hall of the Chosen Slain in Asgard). Over this entrance there resides a wolf and over it there is the head of a boar and on it perches a huge eagle, whose eyes can see to the far regions of the nine worlds. Only those judged worthy by the guardians are allowed to pass through Valgrind. All others are refused entrance. It's not short for 'value grinder', although that's not a bad guess. | |
2. Compiling, installing and configuring | |
| 2.1. When I trying building Valgrind, 'make' dies partway with an assertion failure, something like this: 2.2. When I try to build Valgrind, 'make' fails with/usr/bin/ld: cannot find -lccollect2: ld returned 1 exit status | |
| 2.1. | When I trying building Valgrind, 'make' dies partway with an assertion failure, something like this: |
It's probably a bug in 'make'. Some, but not all, instances of version 3.79.1 have this bug, see www.mail-archive.com/bug-make@gnu.org/msg01658.html. Try upgrading to a more recent version of 'make'. Alternatively, we have heard that unsetting the CFLAGS environment variable avoids the problem. | |
| 2.2. | When I try to build Valgrind, 'make' fails with |
You need to install the glibc-static-devel package. | |
3. Valgrind aborts unexpectedly | |
| 3.1. Programs run OK on Valgrind, but at exit produce a bunch of errors involving __libc_freeres() and then die with a segmentation fault. 3.2. My (buggy) program dies like this: 3.3. My program dies, printing a message like this along the way: 3.4. I tried running a Java program (or another program that uses a just-in-time compiler) under Valgrind but something went wrong. Does Valgrind handle such programs? | |
| 3.1. | Programs run OK on Valgrind, but at exit produce a bunch of errors involving __libc_freeres() and then die with a segmentation fault. |
When the program exits, Valgrind runs the procedure Problem is that running WORKAROUND FOR 1.1.X and later versions of Valgrind: use the | |
| 3.2. | My (buggy) program dies like this: |
If Memcheck (the memory checker) shows any invalid reads, invalid writes and invalid frees in your program, the above may happen. Reason is that your program may trash Valgrind's low-level memory manager, which then dies with the above assertion, or something like this. The cure is to fix your program so that it doesn't do any illegal memory accesses. The above failure will hopefully go away after that. | |
| 3.3. | My program dies, printing a message like this along the way: |
Older versions did not support some x86 instructions, particularly SSE/SSE2 instructions. Try a newer Valgrind; we now support almost all instructions. If it still happens with newer versions, if the failing instruction is an SSE/SSE2 instruction, you might be able to recompile your program without it by using the flag Another possibility is that your program has a bug and erroneously jumps to a non-code address, in which case you'll get a SIGILL signal. Memcheck may issue a warning just before this happens, but they might not if the jump happens to land in addressable memory. | |
| 3.4. | I tried running a Java program (or another program that uses a just-in-time compiler) under Valgrind but something went wrong. Does Valgrind handle such programs? |
Valgrind can handle dynamically generated code, so long as none of the generated code is later overwritten by other generated code. If this happens, though, things will go wrong as Valgrind will continue running its translations of the old code (this is true on x86 and AMD64, on PPC32 there are explicit cache flush instructions which Valgrind detects). You should try running with Alternativaly, if you have the source code to the JIT compiler you can insert calls to the Apart from this, in theory Valgrind can run any Java program just fine, even those that use JNI and are partially implemented in other languages like C and C++. In practice, Java implementations tend to do nasty things that most programs do not, and Valgrind sometimes falls over these corner cases. If your Java programs do not run under Valgrind, even with | |
4. Valgrind behaves unexpectedly | |
| 4.1. My program uses the C++ STL and string classes. Valgrind reports 'still reachable' memory leaks involving these classes at the exit of the program, but there should be none. 4.2. The stack traces given by Memcheck (or another tool) aren't helpful. How can I improve them? 4.3. The stack traces given by Memcheck (or another tool) seem to have the wrong function name in them. What's happening? | |
| 4.1. | My program uses the C++ STL and string classes. Valgrind reports 'still reachable' memory leaks involving these classes at the exit of the program, but there should be none. |
First of all: relax, it's probably not a bug, but a feature. Many implementations of the C++ standard libraries use their own memory pool allocators. Memory for quite a number of destructed objects is not immediately freed and given back to the OS, but kept in the pool(s) for later re-use. The fact that the pools are not freed at the exit() of the program cause Valgrind to report this memory as still reachable. The behaviour not to free pools at the exit() could be called a bug of the library though. Using gcc, you can force the STL to use malloc and to free memory as soon as possible by globally disabling memory caching. Beware! Doing so will probably slow down your program, sometimes drastically.
There are other ways to disable memory pooling: using the
| |
| 4.2. | The stack traces given by Memcheck (or another tool) aren't helpful. How can I improve them? |
If they're not long enough, use If they're not detailed enough, make sure you are compiling with Also, for leak reports involving shared objects, if the shared object is unloaded before the program terminates, Valgrind will discard the debug information and the error message will be full of Also, Some example sub-traces:
| |
| 4.3. | The stack traces given by Memcheck (or another tool) seem to have the wrong function name in them. What's happening? |
Occasionally Valgrind stack traces get the wrong function names. This is caused by glibc using aliases to effectively give one function two names. Most of the time Valgrind chooses a suitable name, but very occasionally it gets it wrong. Examples we know of are printing 'bcmp' instead of 'memcmp', 'index' instead of 'strchr', and 'rindex' instead of 'strrchr'. | |

5. Memcheck doesn't find my bug | |
| 5.1. I try running 'valgrind --tool=memcheck my_program' and get Valgrind's startup message, but I don't get any errors and I know my program has errors. 5.2. Why doesn't Memcheck find the array overruns in this program? | |
| 5.1. | I try running 'valgrind --tool=memcheck my_program' and get Valgrind's startup message, but I don't get any errors and I know my program has errors. |
There are two possible causes of this. First, by default, Valgrind only traces the top-level process. So if your program spawns children, they won't be traced by Valgrind by default. Also, if your program is started by a shell script, Perl script, or something similar, Valgrind will trace the shell, or the Perl interpreter, or equivalent. To trace child processes, use the If you are tracing large trees of processes, it can be less disruptive to have the output sent over the network. Give Valgrind the flag Obviously you have to start the listener process first. See the manual for more details. Second, if your program is statically linked, most Valgrind tools won't work as well, because they won't be able to replace certain functions, such as malloc(), with their own versions. A key indicator of this is if Memcheck says: when you know your program calls malloc(). The workaround is to avoid statically linking your program. | |
| 5.2. | Why doesn't Memcheck find the array overruns in this program? |
Unfortunately, Memcheck doesn't do bounds checking on static or stack arrays. We'd like to, but it's just not possible to do in a reasonable way that fits with how Memcheck works. Sorry. | |

6. Miscellaneous | |
| 6.1. I tried writing a suppression but it didn't work. Can you write my suppression for me? 6.2. With Memcheck's memory leak detector, what's the difference between 'definitely lost', 'possibly lost', 'still reachable', and 'suppressed'? | |
| 6.1. | I tried writing a suppression but it didn't work. Can you write my suppression for me? |
Yes! Use the If you really want to write suppressions by hand, read the manual carefully. Note particularly that C++ function names must be | |
| 6.2. | With Memcheck's memory leak detector, what's the difference between 'definitely lost', 'possibly lost', 'still reachable', and 'suppressed'? |
The details are in the Memcheck section of the user manual. In short:
| |
7. How To Get Further Assistance | |
Please read all of this section before posting. If you think an answer is incomplete or inaccurate, please e-mail valgrind@valgrind.org. Read the appropriate section(s) of the Valgrind Documentation. Read the Distribution Documents. Search the valgrind-users mailing list archives, using the group name Only when you have tried all of these things and are still stuck, should you post to the valgrind-users mailing list. In which case, please read the following carefully. Making a complete posting will greatly increase the chances that an expert or fellow user reading it will have enough information and motivation to reply. Make sure you give full details of the problem, including the full output of You are in little danger of making your posting too long unless you include large chunks of Valgrind's (unsuppressed) output, so err on the side of giving too much information. Clearly written subject lines and message bodies are appreciated, too. Finally, remember that, despite the fact that most of the community are very helpful and responsive to emailed questions, you are probably requesting help from unpaid volunteers, so you have no guarantee of receiving an answer. | |
Valgrind is a multipurpose code profilingand memory debugging tool for Linux when on the x86 and, as of version 3,AMD64, architectures. Itallows you to run your program in Valgrind's own environment that monitorsmemory usage such as calls to malloc and free (or new and delete in C++). Ifyou use uninitialized memory, write off the end of an array, or forget to freea pointer, Valgrind can detect it. Since these are particularly commonproblems, this tutorial will focus mainly on using Valgrind to find thesetypes of simple memory problems, though Valgrind is a tool that can do a lotmore.
Alternatively, for Windows users who wantto develop Windows-specific software, you might be interested in IBM's Purify, which hasfeatures similar to Valgrind for finding memory leaks and invalid memoryaccesses. A trial download is available.
Getting Valgrind
If you're running Linux and you don't have a copy already, you can getValgrind from the Valgrinddownload page.Installation should be as simple as decompressing and untarring using bzip2(XYZ is the version number in the below examples)which will create a directory called valgrind-XYZ; change into that directoryand runNow that you have Valgrind installed, let's look at how to use it.
Finding Memory Leaks With Valgrind
Memory leaks are among the most difficult bugs to detect because they don'tcause any outward problems until you've run out of memory and your call tomalloc suddenly fails. In fact, when working with a language like C or C++that doesn't have garbage collection, almost half your time might be spenthandling correctly freeing memory. And even one mistake can be costly ifyour program runs for long enough and follows that branch of code.Valgrind Lr
When you run your code, you'll need to specify the tool you want to use;simply running valgrind will give you the current list. We'll focus mainly onthe memcheck tool for this tutorial as running valgrind with the memcheck toolwill allow us to check correct memory usage. With no other arguments, Valgrind presents a summary of calls to free andmalloc: (Note that 18490 is the process id on my system; it will differbetween runs.)If you have a memory leak, then the number of allocs and the number of freeswill differ (you can't use one free to release the memory belonging to morethan one alloc). We'll come back to the error summary later, but for now,notice that some errors might be suppressed -- this is because some errorswill be from standard library routines rather than your own code.
If the number of allocs differs from the number of frees, you'll want to rerunyour program again with the leak-check option. This will show you all of thecalls to malloc/new/etc that don't have a matching free.
For demonstration purposes, I'll use a really simple program that I'll compileto the executable called 'example1'This will result in some information about the program showing up, culminatingin a list of calls to malloc that did not have subsequent calls to free:This doesn't tell us quite as much as we'd like, though -- we know that thememory leak was caused by a call to malloc in main, but we don't have the linenumber. The problem is that we didn't compile using the -g option of gcc,which adds debugging symbols. So if we recompile with debugging symbols, weget the following, more useful, output:Now we know the exact line where the lost memory was allocated. Although it'sstill a question of tracking down exactly when you want to free that memory,at least you know where to start looking. And since for every call to mallocor new, you should have a plan for handling the memory, knowing where thememory is lost will help you figure out where to start looking.
There will be times when the --leak-check=yes option will not result inshowing you all memory leaks. To find absolutely every unpaired call to freeor new, you'll need to use the --show-reachable=yes option. Its output isalmost exactly the same, but it will show more unfreed memory.
Finding Invalid Pointer Use With Valgrind
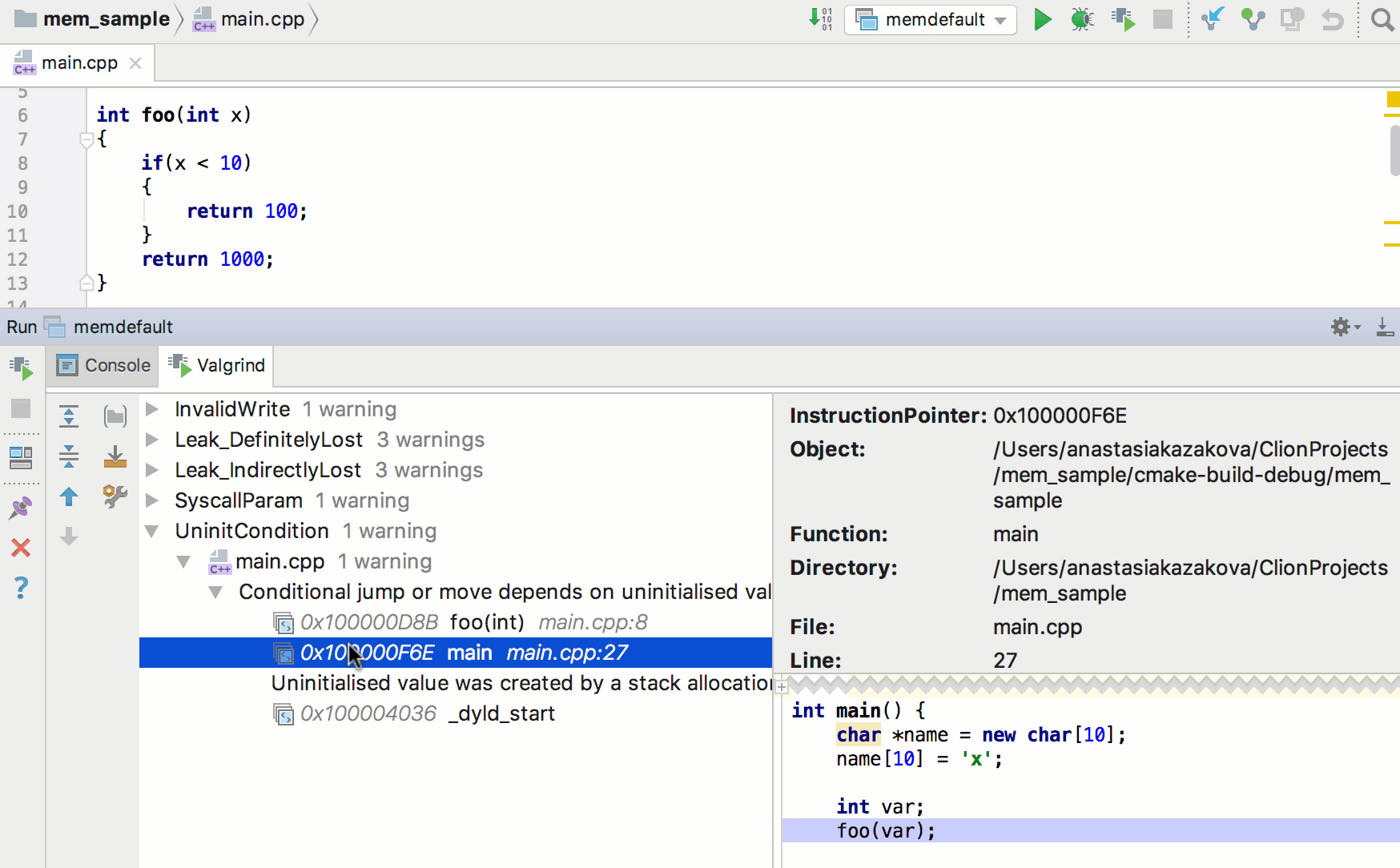
Valgrind can also find the use of invalid heap memory using the memcheck tool.For instance, if you allocate an array with malloc or new and then try toaccess a location past the end of the array:Valgrind will detect it. For instance, running the following program,example2, through Valgrindwithresults in the following warningWhat this tell us is that we're using a pointer allocated room for10 bytes, outside that range -- consequently, we have an 'Invalid write'. Ifwe were to try to read from that memory, we'd be alerted to an 'Invalid readof size X', where X is the amount of memory we try to read. (For a char,it'll be one, and for an int, it would be either 2 or 4, depending on yoursystem.)As usual, Valgrind prints the stack trace of function calls so that we knowexactly where the error occurs.Detecting The Use Of Uninitialized Variables
Another type of operation that Valgrind will detect is the use of anuninitialized value in a conditional statement. Although you should be in thehabit of initializing all variables that you create, Valgrind will help findthose cases where you don't. For instance, running the following code asexample3through Valgrind will result in Valgrind is even smart enough to know that if a variable is assigned the valueof an uninitialized variable, that that variable is still in an'uninitialized' state. For instance, running the following code:in Valgrind as example4 results in the following warning:You might think that the problem was in foo, and that the rest of the callstack probably isn't that important. But since main passes in anuninitialized value to foo (we never assign a value to y), it turns out thatthat's where we have to start looking and trace back the path of variableassignments until we find a variable that wasn't initialized.This will only help you if you actually test that branch of code, and inparticular, that conditional statement. Make sure to cover all executionpaths during testing!
What else will Valgrind Find
Valgrind will detect a few other improper uses of memory: if you call freetwice on the same pointer value, Valgrind will detect this for you; you'll getan error:along with the corresponding stack trace.Valgrind also detects improperly chosen methods of freeing memory. Forinstance, in C++ there are three basic options for freeing dynamic memory:free, delete, and delete[]. The free function should only be matched with acall to malloc rather than a call to, say, delete -- on some systems, you might be able to get away with notdoing this, but it's not very portable. Moreover, the delete keyword should only be paired with the new keyword (for allocation of single objects), and the delete[] keyword should only bepaired with the new[] keyword (for allocation of arrays). (Though some compilers will allow you to get away with using the wrong version of delete,there's no guarantee that all of them will. It's just not part of thestandard.)
If you do trigger one of these problems, you'll get this error: which really should be fixed even if your code happens to be working.
What Won't Valgrind Find?
Valgrind doesn't perform bounds checking on static arrays (allocated on thestack). So if you declare an array inside your function:then Valgrind won't alert you! One possible solution for testing purposes issimply to change your static arrays into dynamically allocated memory takenfrom the heap, where you will get bounds-checking, though this could be a messof unfreed memory.A Few More Caveats
What's the drawback of using Valgrind? It's going to consume more memory --up to twice as much as your program normally does. If you're testing anabsolutely huge memory hog, you might have issues. It's also going to takelonger to run your code when you're using Valgrind to test it. This shouldn'tbe a problem most of the time, and it only affects you during testing. But ifyou're running an already slow program, this might affect you.Finally, Valgrind isn't going to detect every error you have -- if you don'ttest for buffer overflows by using long input strings, Valgrind won't tell youthat your code is capable of writing over memory that it shouldn't betouching. Valgrind, like another other tool, needs to be used intelligentlyas a way of illuminating problems.
Summary
Valgrind is a tool for the x86 and AMD64 architectures and currently runsunder Linux. Valgrind allows the programmer to run the executable inside itsown environment in which it checks for unpaired calls to malloc and other usesofinvalid memory (such as ininitialized memory) or invalid memory operations(such as freeing a block of memory twice or calling the wrong deallocatorfunction). Valgrind does not check use of statically allocated arrays.Related articles
DynamicMemory Allocation, Part 1: Advanced Memory Management
Valgrind Command
Dynamic Memory Allocation, Part 2: Dynamic Memory Allocation and Virtual MemoryDynamic Memory Allocation, Part 3: Customized Allocators with Operator New and Operator Delete
Dynamic Memory Allocation, Part 4: Common Memory Management Problems in C++
UnderstandingPointers